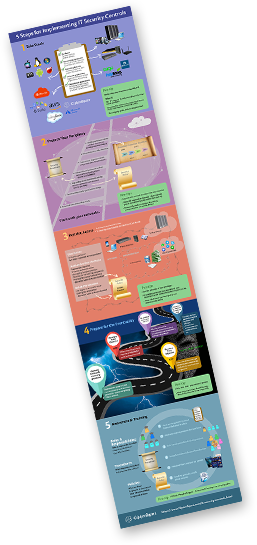
CipherSpace Enterprise IaaS maps to NIST Special Publication 800-53 Rev 4
Cybersecurity is a shared responsibility between CipherSpace and the customer
Cipherspace’s products and services are built on the three fundamental pillars of security – Confidentiality, Integrity, and Availability.
Our security-first approach is a natural outcome of the way we operate:
- driven by experience
- centered on solving customer problems
- committed to protecting our customer’s data and systems
- providing ‘Peace of Mind’
Why did we choose to map to the NIST 800-53 cybersecurity framework?
Once you look at a few facts, the obviousness of our choice will be apparent. NIST Special Publication 800-53 is:
- One of the most robust Cybersecurity Frameworks

Source: Complianceforge
- A multi-year effort to develop next-generation security and privacy controls to protect products and services we depend on, and which support the economic and national security interests of the United States.
- A proactive and systemic approach to developing comprehensive safeguarding measures for all types of computing platforms
- Designed to serve the urgent need to strengthen the trustworthiness and resilience of the information systems
References:
NIST SP 800-53 Rev. 4, Security and Privacy Controls for Federal Info Systems and Organizations
NIST SP 800-53 Rev. 5 (Final), Security and Privacy Controls for Info Systems and Organizations
NIST SP 800-53 also maps [ details in FAQs ] to multiple other industry-specific frameworks like HIPAA, PCI DSS, and international cybersecurity frameworks like GDPR, and ISO 27001. This is another reason, we have chosen to align our best practices with NIST SP 800-53.
Frequently Asked Questions (FAQs)
- What is the Shared Responsibility Model?
Security, by its very nature, is a shared responsibility between CipherSpace and the customer. In the shared responsibility model, CipherSpace takes responsibility for operating and maintaining the host operating system, virtualization layer, and components provided by CipherSpace as part of IaaS. Physical security is maintained by our datacenter provider Equinix. The customer has the responsibility of operating and managing the guest operating system, and application software installed on it, and for configuring access control lists and security groups. Updates and patches of the guest OS, and applications installed on it are also responsibility of the customer.
This shared responsibility model also extends to security controls. In alignment with NIST 800-53 security controls, the following guidelines and examples can be used to assess responsibility ownership.
Controls Fully inherited from CipherSpace – These controls are typically fully operationalized within Cloud Service Provider’s environment.
Physical And Environmental Protection Control: CipherSpace inherits from and augments the controls of Equinix (datacenter service provider).
Controls Shared by the Customer and CipherSpace – These controls typically apply to both the infrastructure layer and customer layers. The responsibility of implementing them is dependent on the environment in which the system and/or application operates.
System And Information Integrity Control: While CipherSpace is responsible for flow remediation through the application of patches and fixes within IaaS infrastructure components, customers are responsible for patching their guest OS and applications.
Access Control: CipherSpace is responsible for account management, separation of duties, access enforcement, and applying the principle of least privileges within its IaaS infrastructure components. Customers should implement these controls to restrict access to guest OS, database, and application components.
Identity and Authentication control: Identifier (typically users and devices) and authenticators (typically passwords and other forms of access tokens) management, and encryption key management for guest OS, databases, applications is the responsibility of a customer. CipherSpace maintains identities and authenticators to manage its IaaS infrastructure.
Configuration Management control: CipherSpace maintains the configuration of its infrastructure components, but a customer is responsible for configuring their own guest operating systems, databases, and applications.
Awareness and Training: We will train our employees. A customer must train their own employees.
Customer-specific controls – Depending on the application and its operating environment, a customer is solely responsible for deploying these controls. Examples include:
Contingency planning: Backup and Disaster Recovery policy along with business continuity planning is the sole responsibility of the customer.
Systems and communications protection: Responsibility of protecting virtual networks, security of communication, and appropriate routing of data within a customer environment lies with a customer. - As a customer, what is my responsibility to secure my systems at CipherSpace?
Refer to answer of ‘What is Shared Responsibility Model?’ - How can CipherSpace help me achieve alignment with the NIST SP 800-53 framework or other compliance standards?
CipherSpace provides consulting services to help assess the current security posture of your systems. We can also work with you to quickly implement best practices aligned with your target compliance standard. - How does NIST SP 800-53 map to other frameworks like HIPAA, GDPR, SOC 2, ISO 27002, NIST CSF, CIS 20, etc.?
Here are a few mappings from dependable sources…
NIST SP 800-53 Rev4 to NIST CSF 1.0 mapping – by NIST ( Excel file )
NIST SP 800-53 Rev4 to NIST CSF mapping – by HITRUST ( PDF file )
NIST CSF to GDPR crosswalk – by NIST ( HTML page)
NIST-Security-HIPAA-Crosswalk – by HHS.gov ( PDF file )
NIST CSF to NIST SP 800-53 , ISO 27001, COBIT 5, ISA 62443 mapping – by NIST ( Excel file )
NIST SP 800-53 to SOC Trust Service Criteria – by AICPA ( Excel file )
Mappings Relevant to the AICPA SOC Suite of Services ( NIST 800-53, ISO 27001, NIST CSF, COBIT5) ( HTML page with individual mapping links )
PCI DSS to NIST CSF, NIST 800-53 and other standards – by pcisecuritystandards.org ( PDF file )
PCI DSS to NIST CSF, NIST 800-53 and other standards – by pcisecuritystandards.org ( Docx file )
NIST SP 800-53 to PCI DSS – by GSASmartPay ( PDF file )
CIS Controls Mapping to the NIST – by Center for Internet Security ( HTML page )
Cybersecurity Maturity Model (Mother of all mappings) – by Complianceforge ( Excel file )
Blogs and infographics that reflect CipherSpace outlook on security and privacy

Layering security to minimize risk

Zero Trust: All that goes underneath