IT Security Controls Infographic
5 Steps To Establish A Solid Foundation For Developing And Implementing IT Security Controls, Policies And Procedures For Organizations Of Any Size.
Let’s face it; designing and implementing Information Technology (IT) Security Controls is not a priority for most organizations. This is especially true for Startups, and Small to Medium Enterprise, who focus their energy on getting their ideas to market and on growth.
In my experience, the thought of having codified IT Security Policies and Procedures is triggered, more often than not, when the absence of it becomes a deal-breaker in a Sales Cycle.
Even when the need for IT security is clearly understood and established, many organizations struggle to establish a good starting point.
The struggle is understandable. I’ve experienced it myself. I’ve walked down the path, gotten lost, felt like I got back on track only to go around in circles until I finally landed somewhere that felt solid and reassuring.
This blog is my attempt to share what I’ve learned in the process. I hope it serves as a guide to anyone who needs clarity getting started.
Or, watch this explainer video for a quick overview:
Why Security Controls?
Imagine that you need to secure your home. Ask yourself,
- Why am I securing the home? Very likely, it is because you perceive some threats.
- What are the threats to your home? Break-in, theft of valuables, losing your home altogether (hurricane, fire, flood, other), etc.
- What happens if the threat materializes? i.e., What is the risk?
- What are the first five steps you are likely to take to secure your home to manage the risks you’ve identified?
The First 5 Steps You Might Take To Secure Your Home
1) Take stock of your household. List the valuables within the boundaries of your home that you would like to protect.
2) Protect the periphery. Make sure that certain unwanted elements don’t come in. You might put up a wall, install a barbed-wire fence, add gates.
3) Restrict further access. You could add gate codes, garage door codes, video surveillance at entry points, video doorbells, locks with keys for every room. And so on and so forth, based on your perception of the value of things you are protecting.
4) Recovery plan if the threat becomes real. Let’s say a break-in happens, or a wildfire starts in the vicinity. You might have an emergency bag of essentials at the ready, take out the appropriate insurance, move valuables to bank lockers, or anything else that lets you sleep in peace, knowing that the risk is down to a level you can accept.
5) Educate every member of the household, so they are aware of their role in keeping the house secure. Train them on how to operate and maintain all devices of security and respond when a threat materializes. Without this awareness and training, none of the steps taken are useful.
You may notice that some of these are already in place for your home, but you never thought about it consciously. It is human nature to seek safety and protect what one considers dear and near.
Apply This Thinking To Your IT Security.
Like your home security, you may discover that your sysops team (or sysadmins) have already put in place basic security or better. It is their second nature, and codifying what is already in place, is a great place to start. You might be surprised that more than 50% of what is needed is already in place. It just needs to be formalized.
The first 5 steps for securing your Information Technology (IT security) are going to very much align with what you do to secure your home.
1) Take stock – Get to know the expanse of your Information Systems. Take Inventory of your hardware and software.
2) Protect your periphery – List your networks and protect all entry and exit points. (Systems and Network Security Policy)
3) Restrict access – Implement strong passwords, encryption, and role-based access control (identity and Access Control Policy)
4) Prepare for the eventuality – Have a backup and recovery plan that is well documented and, more importantly, well tested. (Backup and Recovery Plan and Incident Response Policy)
5) Awareness and Training – Make sure that each employee/contractor knows what steps are in place for IT security, and their role in maintaining the state of security. (Awareness and Training program)
If you get it, you can stop reading this blog at this point. If you are interested in more details about steps 1 thru 5, read on.
A very quick primer on policies and procedures
Policy: Is a statement of Intent. It is defined to guide decisions. For example, All users accessing our IT resources should be authenticated.
Procedure: Repeatable tasks that implement the guidance given by policies. For example, All IT resources must be configured to require strong passwords at the time of provisioning.
Technical Details Of The First 5 Steps Of IT Security
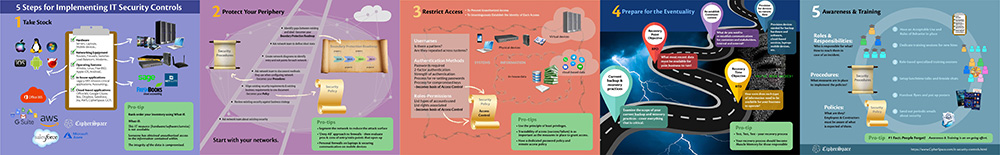
1) Take Stock – This is a preparation step. It is about doing the legwork to develop the right kind of IT security policies and procedures – the ones that are best suited to meet your requirements.
Take Stock – The what:
To secure something, you need first to know what to secure. Having an inventory of IT resources is helpful. Typical candidates for Inventory are,
- Hardware – Servers, Laptops, Mobile Devices
- Networking Equipment – Routers, Firewalls, Switches, VPN concentrators, Load balancers, Modems
- Operating Systems – Windows, Linux, Free BSD, Apple iOS, Android, etc.
- In-house application software – Legacy ERP solutions, In-house mission-critical applications, Accounting software, etc.
- Cloud-based Services used – IaaS, SaaS, PaaS, or any other ‘X’aaS
Take Stock – The how:
- Start with company-owned IT resources. In today’s world, this is anything that has an IP address and is critical to running your business. If you have a smart coffee machine – it is okay to drop it from this list unless you are in the business of selling coffee made from smart coffee machines!
- Now add 3rd party cloud-based services on which you depend to run your business smoothly, these could be:
- Mail, messaging and productivity tools like office 365 or Google Gsuite
- Cloud-based storage like Box, Dropbox, OneDrive
- SaaS like Salesforce, Workday, Jira, Github
- IaaS like CipherSpace, AWS, Azure, GCP. You get the idea.
- Use Tools to automate and update and maintain hardware and software inventory.
- When you start, don’t worry too much about what details to include in the Inventory. Collect what you can as efficiently as possible. For example, automating the collection process, or consolidating a list of all your purchases in a spreadsheet.
Pro Tip:
Rank order your Inventory in terms of its value to your business. The best way to think about it is by doing a ‘What-If.’
- What-if: This IT resource (hardware/software/service) is not available.
- What-if: Someone has obtained unauthorized access to the information contained within.
- What-if: The integrity of the data is compromised.
Look at the CIA (Confidentiality, Availability, Integrity) of the IT resources – it helps you prioritize your efforts for the next steps.
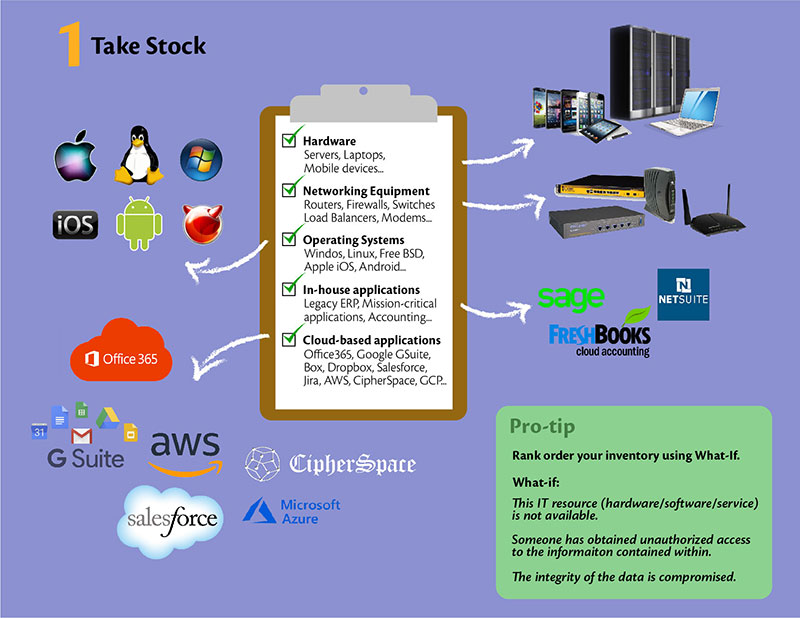
2) Protect your Periphery – It is common sense to secure the periphery before moving to secure individual valuable items. In IT security parlance, this would be equivalent to developing a ‘System and Communications Protection Policy and Procedures’ (a.k.a. Systems and Networks Security Policies and Procedures).
Protect your Periphery – The what:
- Start with your networks. Make sure to include all your locations, including cloud-based IaaS.
- Next, secure entry and exit points through which your valuable information enters or leaves the boundaries of your organization.
- Then secure personal devices used for work, i.e., laptops, mobility devices – these often move in and out of the organization’s defined boundaries, even extending them to cafes, hotels, libraries, public transport systems.
The very concept of “periphery” for you may be dynamic and shifting, and you need to be aware of it before moving to the how.
Protect your Periphery – The how:
- Bring the team that manages your networks to the table. Ask them what has been put in place to secure the network.
- More importantly, ask why they did what they did – their answer shows their Intent. Check if that aligns with the Intent at the business and strategy level. Merge the two, and most likely that is your policy.
- Ask the team to document the guidance/principles they are using when configuring and securing your network resources. This becomes a starting point for your procedures. E.g., In-bound access to employees/contractors shall be enabled only using encrypted VPN.
- Get your network diagrams in place with clear identification of entry and exit points for each network. Include as many details as you have about the current state of affairs.
- Once you have documented AS-IS, ask your team about what is the ideal state for periphery protection, and what is the gap? Discuss the trade-offs keeping in mind risk v/s reward of implementing a particular security feature. This becomes the basis of your roadmap for enhancing boundary protection.
- Include details about:
- Internal boundaries (For e.g., voice and data VLANs, Department wise VLANs, Protections put in place between databases and application servers),
- Encryption technologies in place to protect all communications.
Pro Tip:
- Segmenting the network to reduce the attack surface is always a good idea.
- ‘Deny All’ approach is the norm when it comes to firewall policies. This forces you to carefully weigh the pros and cons of every entry/exit point that is opened up.
- Consider implementing a personal firewall on laptops and securing communication on mobile devices that extends your organization boundaries in public places.
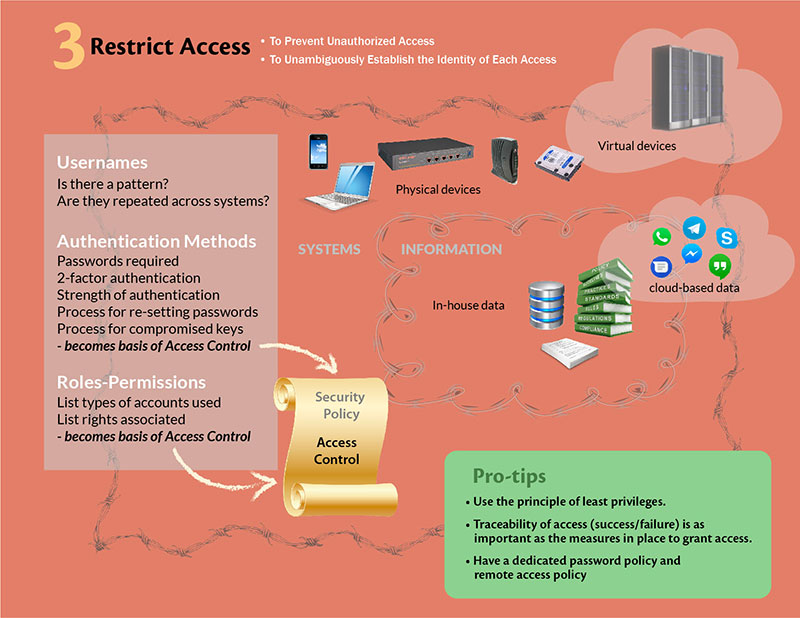
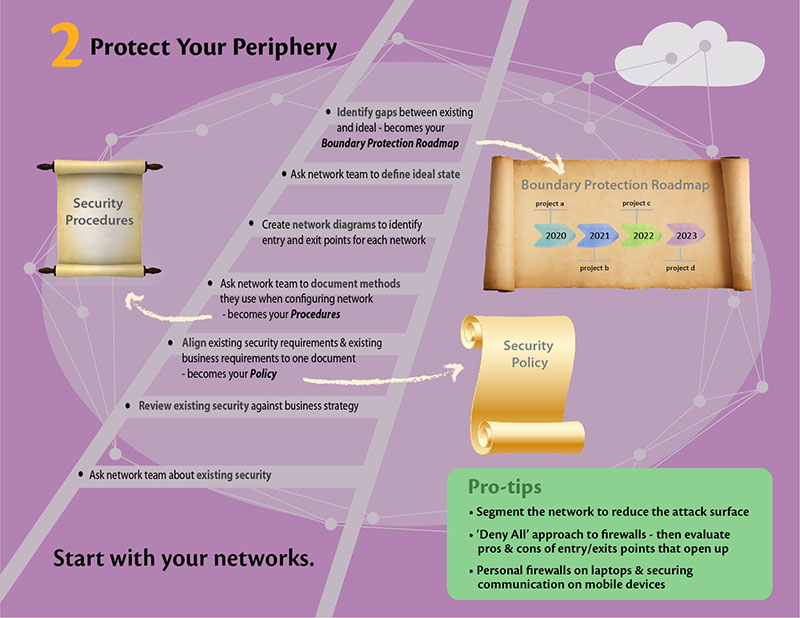
3) Restrict Access – When you are confident that your boundaries are secure, the next logical step is to further restrict access to who can enter within the boundaries, and once in, to which IT resources and data they have access. Again, this is a very logical next step, and every organization, including yours, have written or unwritten rules about granting access, so start by noting them down and making it official. This gives you your AS-IS ‘Identity and access management’ policy.
Restrict Access – The what:
- Access to Systems – All devices, physical or virtual, are in scope. Include servers, storage devices, networking devices, mobile devices.
- Access to Information – Documents, code, contracts, legal stuff, emails, IMs, CRMs, HR – all the important data that makes your business run is in scope here. Make sure to include in-house and cloud-based data.
Restrict Access – The how:
- Look at the usernames that are being used to access any information in your organization. Do they have a pattern? JDoe, Jane Doe, Jane_Doe, JaneD…. Is it consistent across systems and applications? Is it the same even for service provided by 3rd party SaaS vendors? Once you have the data, the emerging patterns become the basis of identity management policy.
- Add to this the type of authentication mechanisms used. Most common are passwords; you may have enabled two-factor authentications for some of the critical applications. The strength of authenticators, cryptography used, processes around resetting lost passwords, or revoking compromised keys – will become a section on your policy and procedures about authenticator management.
- Next is to list down types of accounts used (normal user, admin, HR users, finance users, sales, etc.) and type of rights that are associated with each account type. This forms the basis of the access control section of the policy.
- Now talk to your team about why have they put these measures in place. The answers are the basis of the access control section of your policy.
Pro Tip:
Understand why we are even thinking about restricted access. One – to prevent unauthorized access, and Two – to unambiguously establish the identity of each access.
- Use the principle of least privileges – the access rights granted should not be higher than that needed to accomplish assigned business functions.
- Traceability of access (success/failure) is as important as the measures in place to grant access.
- Consider having a dedicated password policy and remote access policy. Having it in place makes the evaluator more comfortable with your efforts on implementing policies.
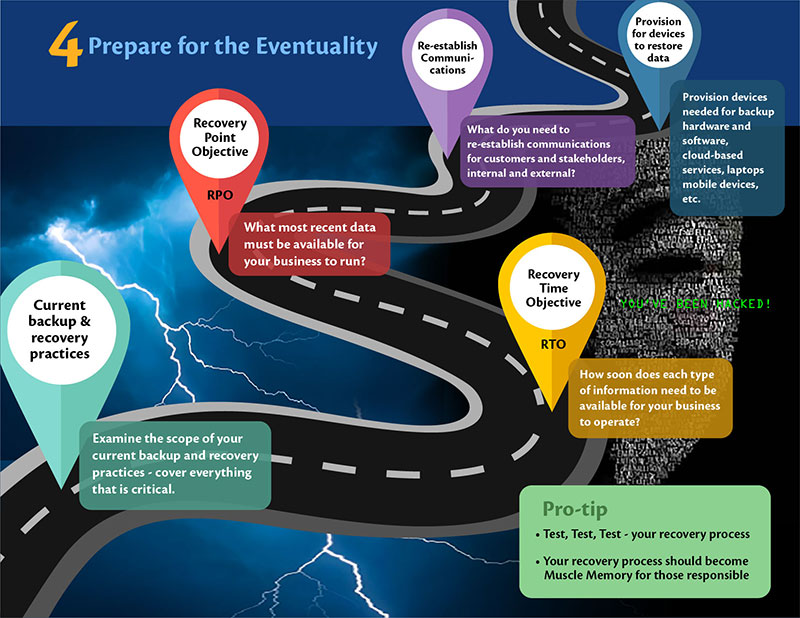
4) Prepare for the Eventuality – Unwanted incidents do happen. The level of preparedness in the event of an incident determines the level of impact your business will suffer on the other side of the incident. The question is: are you prepared? And more importantly, why is there a need to prepare? The deeper you get into “why”, the better articulation you have in your ‘Incident Response policy.’ It gives you an alignment of the strategic needs with the efforts and cost spent in putting up an ‘Incident Response Plan.’
Prepare for the Eventuality – The what:
- At a minimum, everything that is critical to operating your business during the incident:
- Systems, information, and communication.
- Better, everything that is needed to ensure that your business can be reconstituted to pre-incident level:
- Systems, information, communication, places, and people.
- Rank ordering of inventory you did in ‘Take a stock’ step would come in handy in determining what is critical.
Prepare for the Eventuality – The how:
- Examine the scope of current backup and recovery practices. Does it include all the critical information at the least? If not, expand the scope to cover everything that is critical.
- Determine how soon you would want which type of information to be made available in case of an incident, for your business to operate. This would establish Recovery Time Objective (RTO) for each information type.
- What is the most recent data that must be available for your business to run? For e.g., if you change your list prices once a year, the list price data can be as old the last time it was changed. On the other hand, if you are handling multiple quotes a day, your quoting systems should be as recent as day old. This would give you your RPO (Recovery Point Objective).
- Think through what measures you need to take to re-establish communication between your customers and stakeholders, both internal and external.
- Make sure to provision for devices needed to restore data. This would include backup hardware and software, cloud-based services, laptops, mobile devices, and so on.
Pro Tip:
Test, test, test. If you have not tested your recovery processes, there is a high probability that things will go wrong when needed the most. The recovery process should become muscle memory for those who are responsible for it.
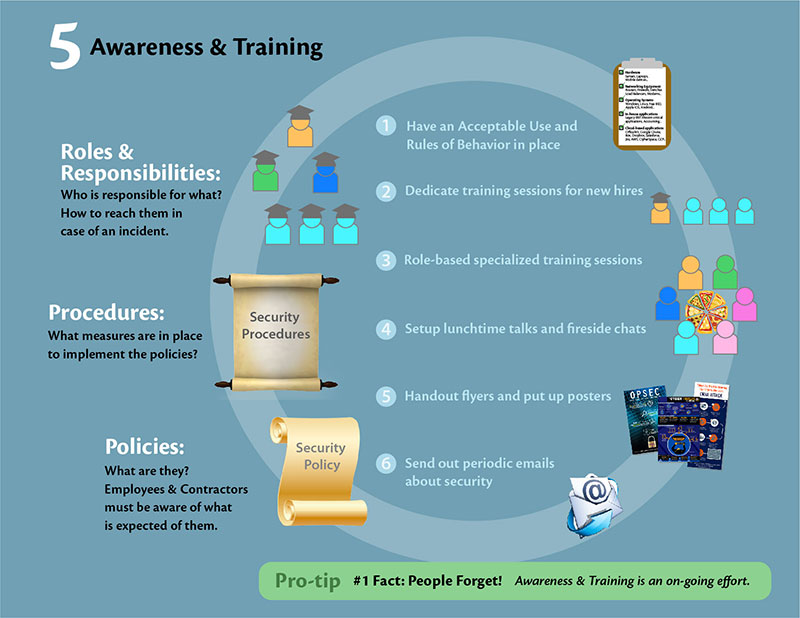
5) Awareness and Training – Imagine you have state-of-the-art technology in place at a healthcare center, but the staff is not trained on how to operate this technology. You will be in a similar situation if you spend time and effort in putting policies and procedures in place, and then stop! Outside the handful who were involved in drawing up and implementing policies and procedures, the larger organization will remain unaware, and that defeats the purpose of the entire initiative.
Awareness and Training – The what:
- Policies – What are they and why they are in place. Employees and contractors must be aware of policies and what is expected of them.
- Procedures – What measures are in place to implement the Intent stated in policies.
- Roles and responsibilities – Who is responsible for what and how to reach them in case of questions, clarifications, or incident.
Awareness and Training – The how:
- Have an ‘Acceptable Use’ and ‘Rules of Behavior’ in place.
- Dedicated training sessions about InfoSec at the time of onboarding.
- Create role-based specialized training if needed to ensure that employees are prepared to handle responsibilities assigned to them.
- Set up lunchtime talks and fireside chats.
- Hand out flyers and put up posters.
- Send out periodic email communications.
- Apply any other innovative ideas you can come up with.
Pro Tip:
Always remember one fact – people forget! Awareness and training should be an on-going effort and delivered with whatever innovation necessary to ensure that the message gets across and sticks!
CONCLUSION
Having IT security policies and procedures is no longer optional. It is also not the priority for most organizations unless forced by regulation or demanded by prospects in sales cycles. Starting with the five steps listed in this blog will not only give you a quick start but also quickly take you to a level that you can build on. More importantly, you will have material to keep your sales cycle moving.
A Security-first approach is in our DNA. CipherSpace provides CyberSecurity Implementation services including prioritizing IT security policies and controls aligned with your business priorities. We can take the pressure off your security concerns by managing various aspects of your company’s infrastructure, such as Managed Networks and Managed Databases.